4. Entra ID Extended Services
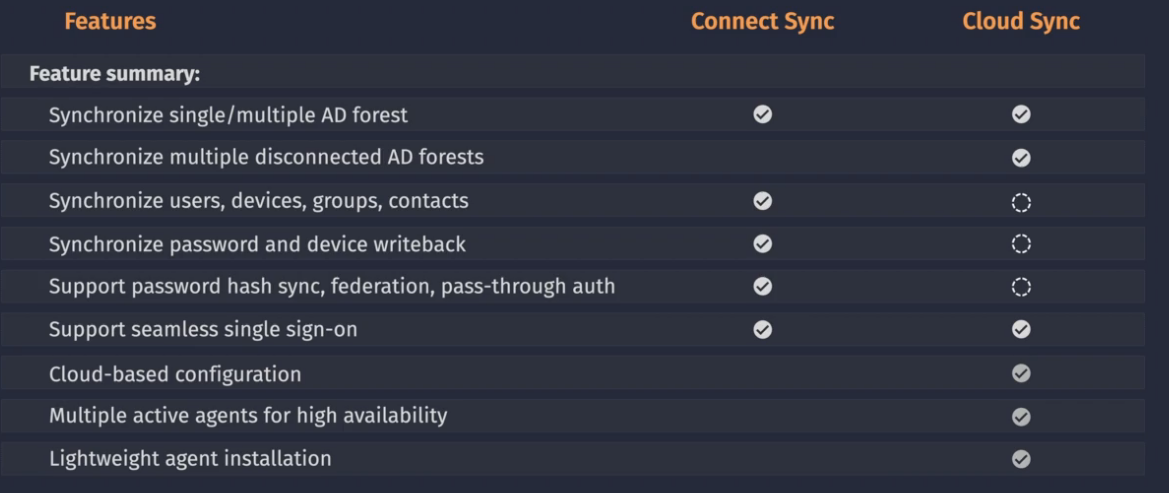
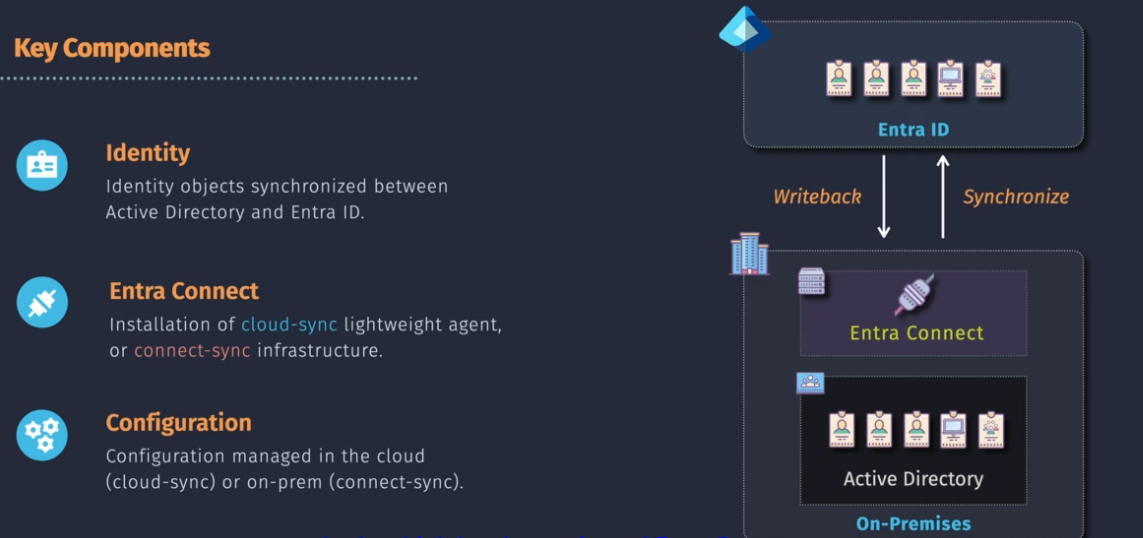
Entra Connect
Used to sync between AD and Entra ID
Two sync service tools:
- Entra Connect Sync
- Entra Connect Cloud Sync
Additional tool called Entra Connect Health.
Entra Domain Services
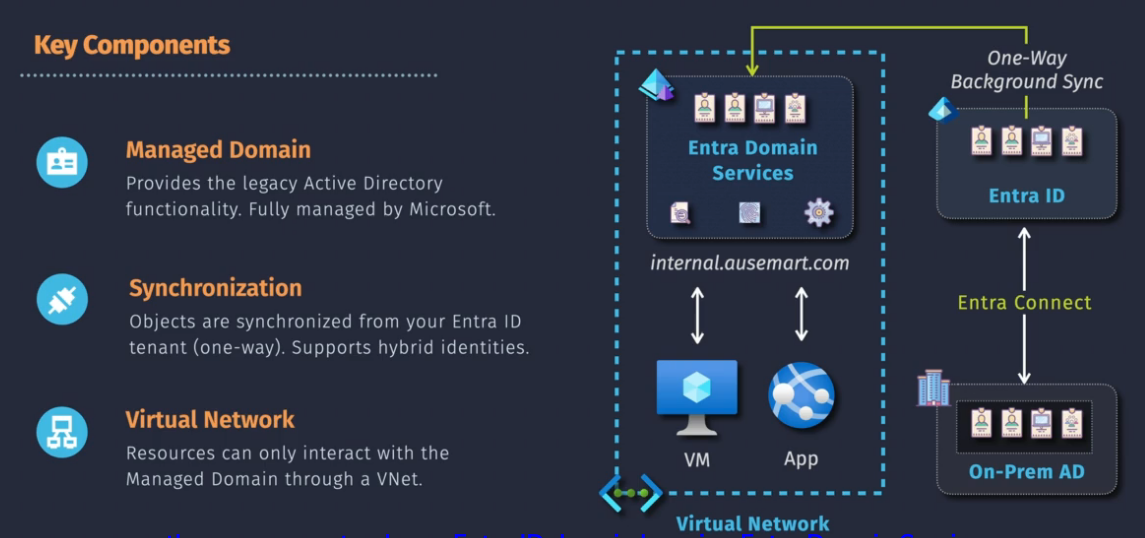
If you need some support for legacy AD domain services, you can build out a cloud based AD instead of deploying your own domain.
You can then connect Entra ID to your on prem via Entra Connect.
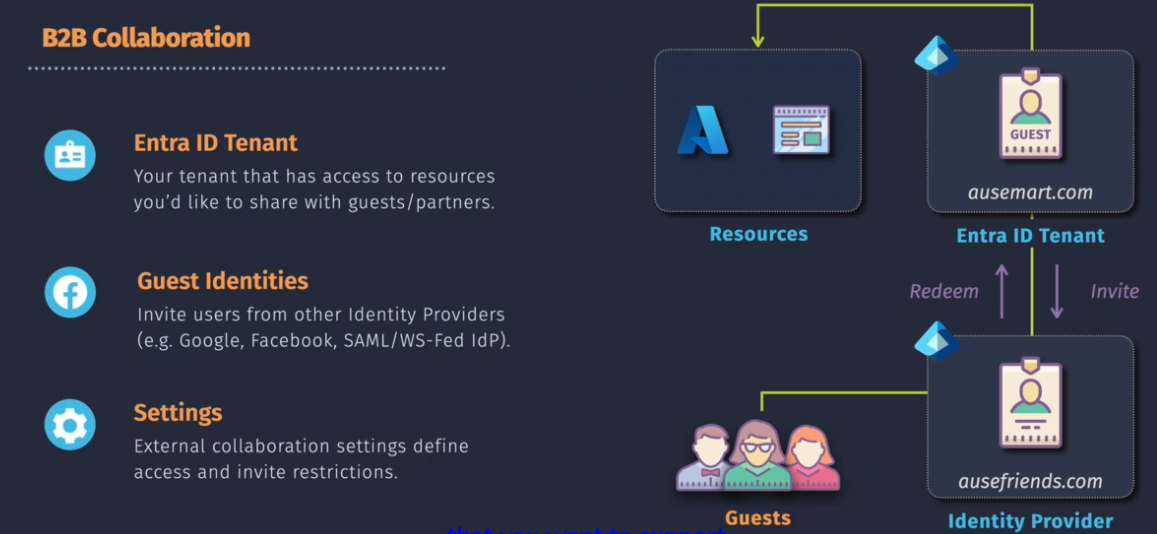
Entra ID External Identities
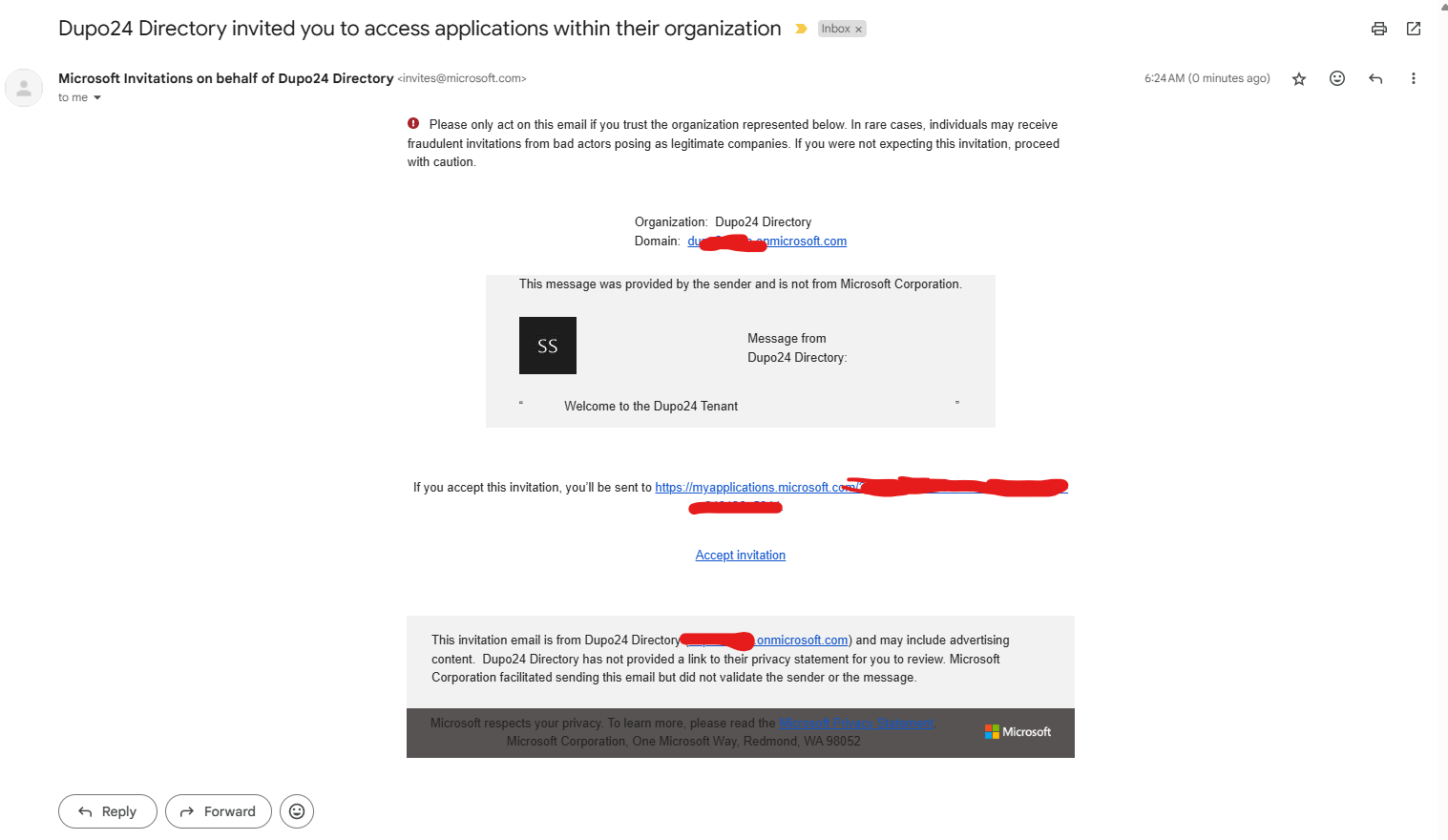
Business to business collaboration - B2B - access to our resources from another tenant or another identity provider.
We can invite the guest user and that user can then accept that invitation to our tenant.
B2B Direct Connect - Teams integration - Trusted organization with another Entra ID tenant.
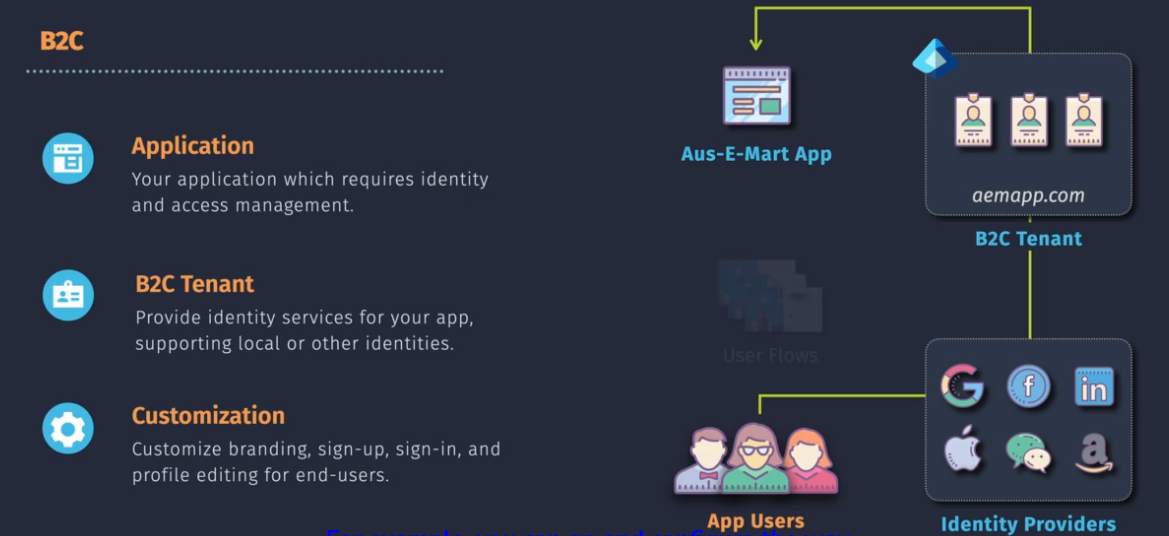
Business to consumer - B2C - identity for an app YOU are developing.
Demo - Invite a guest with B2B Collaboration
Create a test user in one tenant Invite the user from the other tenant Redeem the invitation from the test user Sign in and view from the test user cross tenant.
Remember you are creating a guest identity in your tenant that the external user can use.
Demo - Configure B2B collaboration with Google
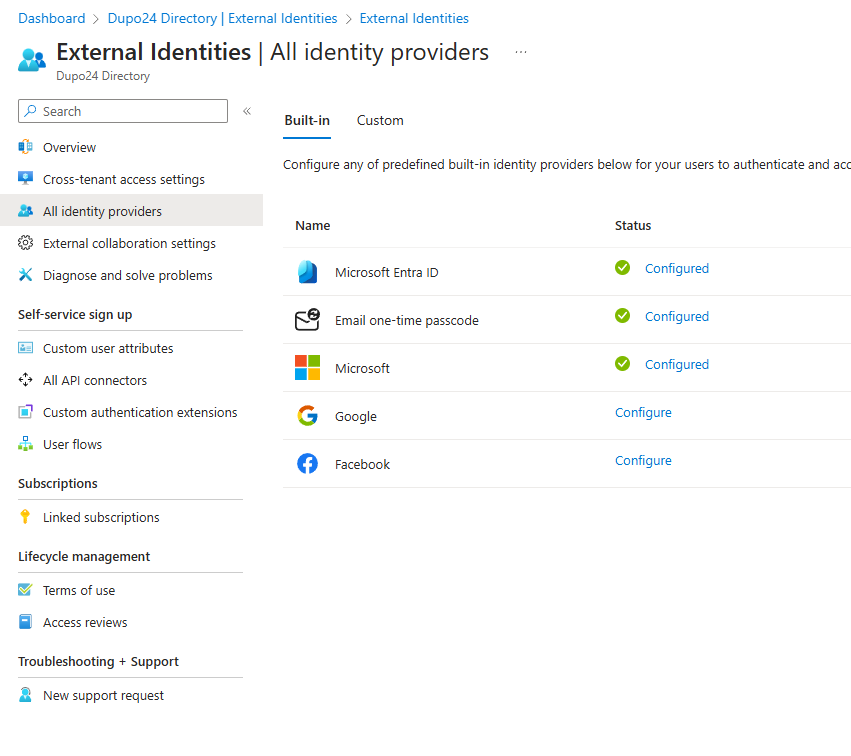
In Google:
 Email invite:
Email invite:
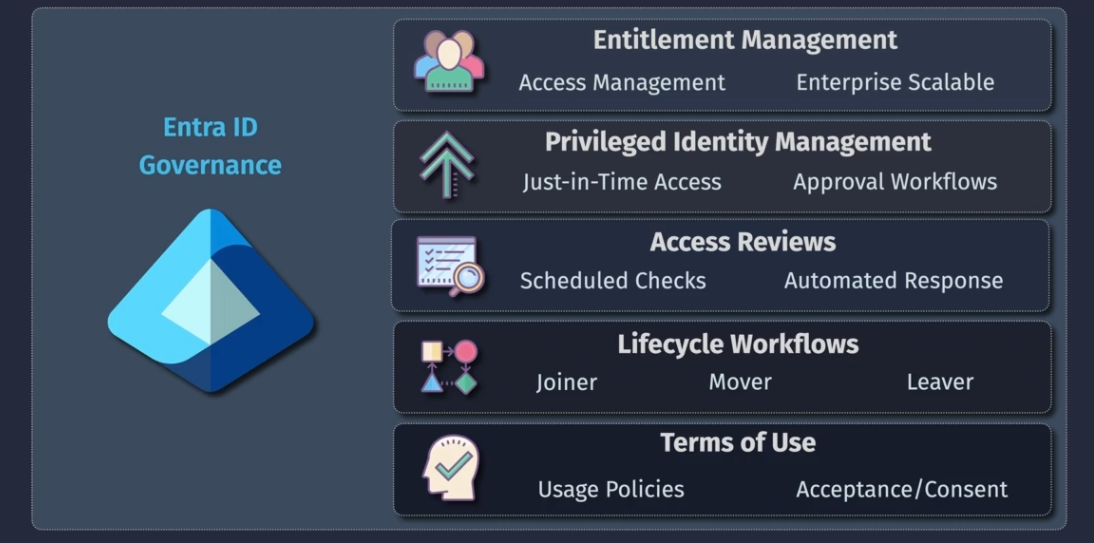
Entra ID Governance Overview
- Entitlement management - access managment
- Privileged Identity Management - PIM - JIT access
- Access Reviews - scheduled checks
- Lifecycle Workflows - Joining, moving, leaving
- Terms of use - Usage policies, acceptance and consent.
Licensing required:
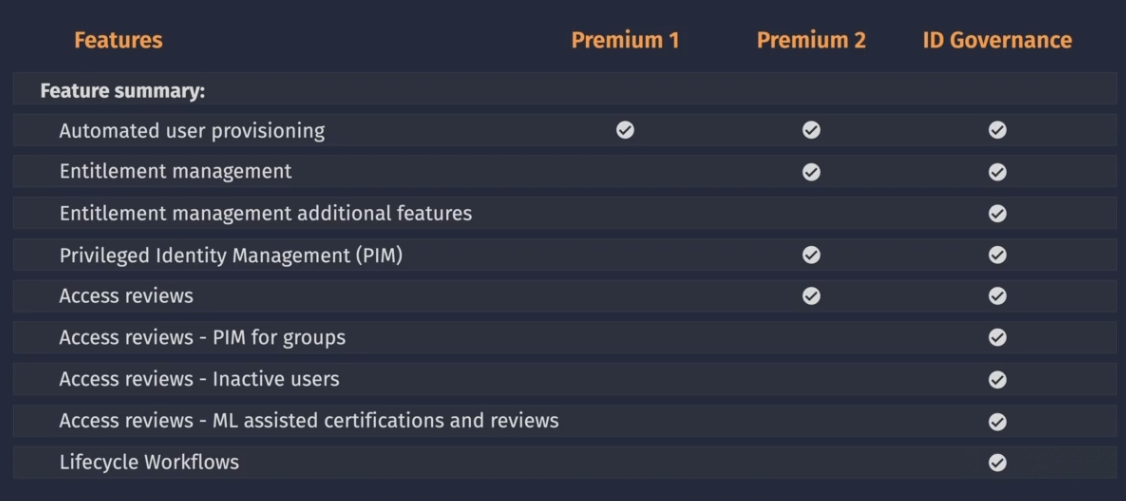
Entra ID Entitlement Management
Simplifies how entitlement is managed at scale.
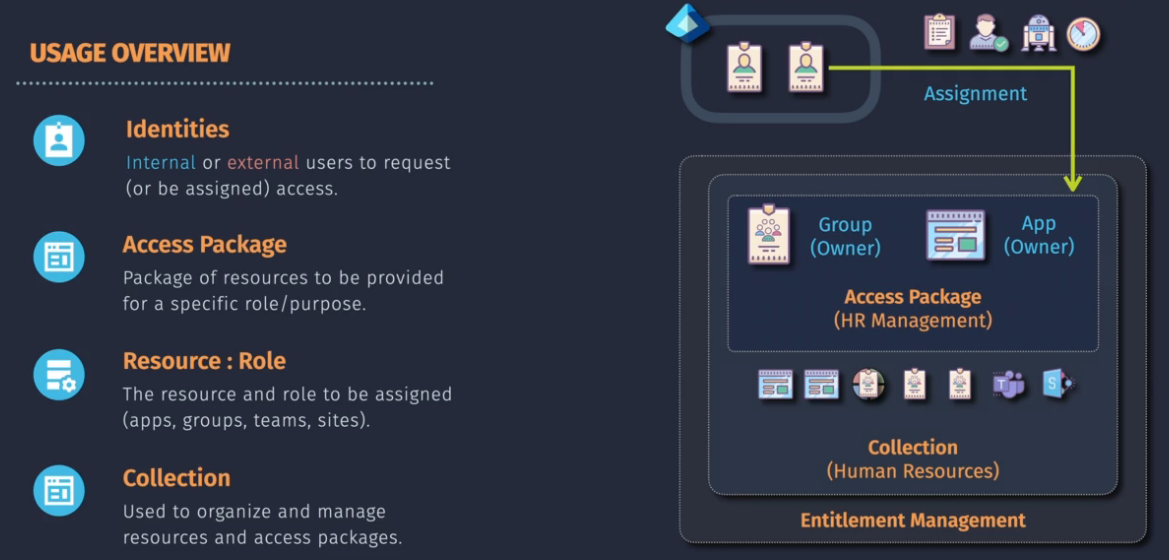
Licensed feature: Identity Governance license
- Licenses are required for those who review, request, assigned a package
- Access packages are created in the portal. Managed via myaccess.microsoft.com
- Permissions: Identity Gov Admin, Access Package Manager
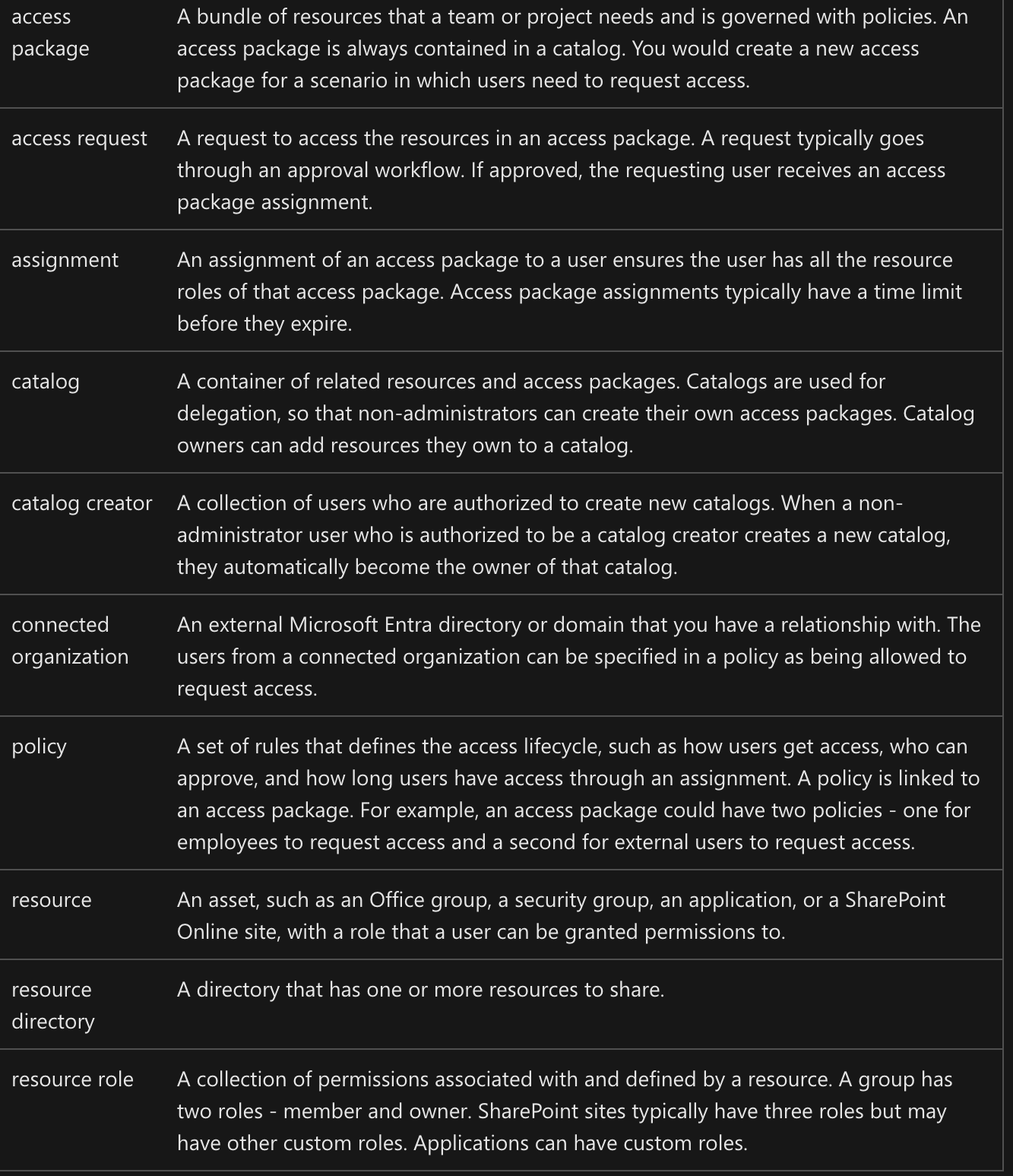
Terms:
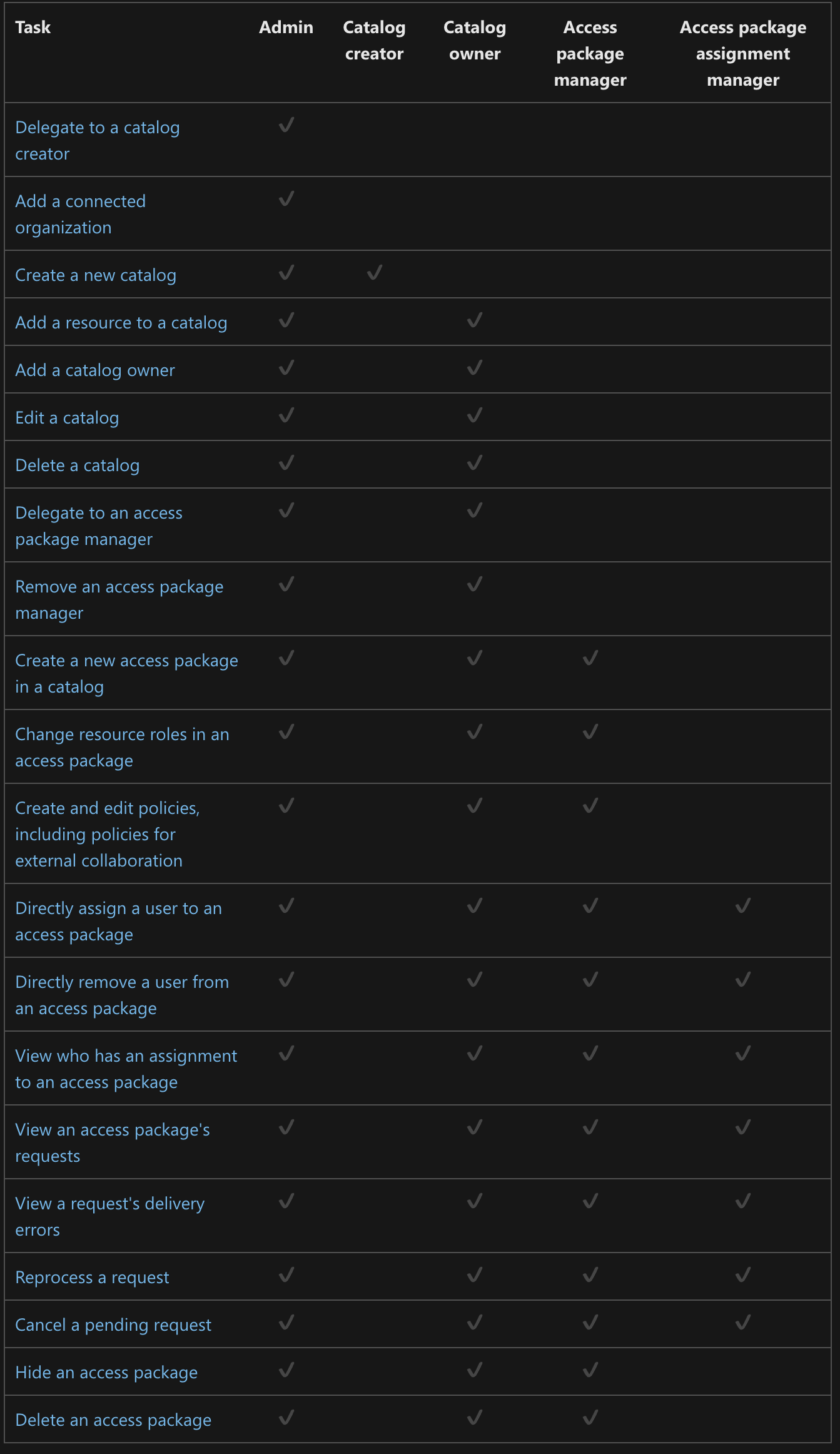
Roles and responsibilities:
Demo - Create and use an access package
Need to watch that video again - we don't use this
Entra ID Privileged Identity Management (PIM)
Just in time access for permissions
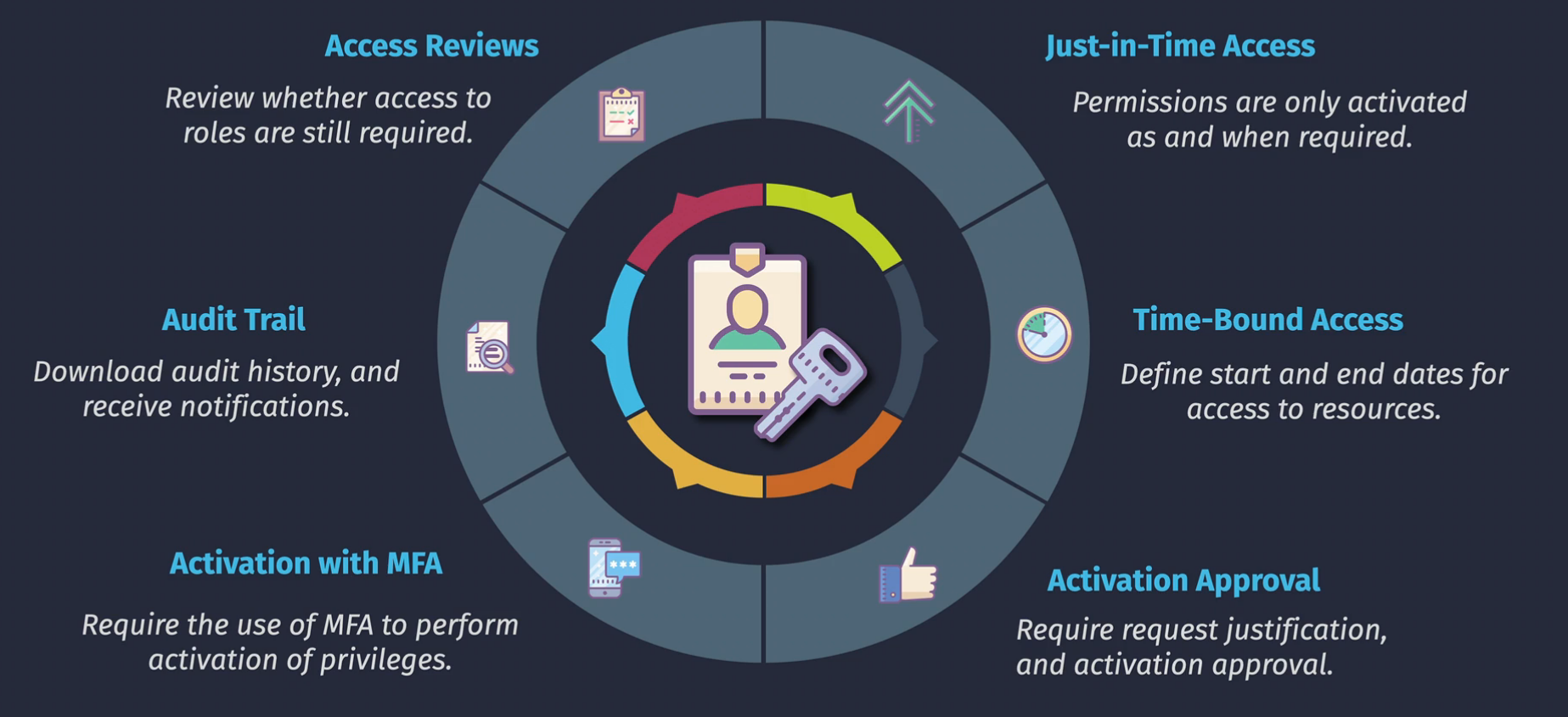
- Identity - eligible for permissions
- Assignment - active or eligible
- Activation - request to turn those permissions on, can have approvals, MFA.
Demo - Entra ID PIM
- Eligible
- Active
- Expired
Can activate with or without approval, add ticket number, justification, etc. Can also deactivate the role if needed.
Entra ID Access Reviews
Over time, loose permissions linger on users as they move through projects or teams. Access Reviews assist with the lifecycle management of these permissions.
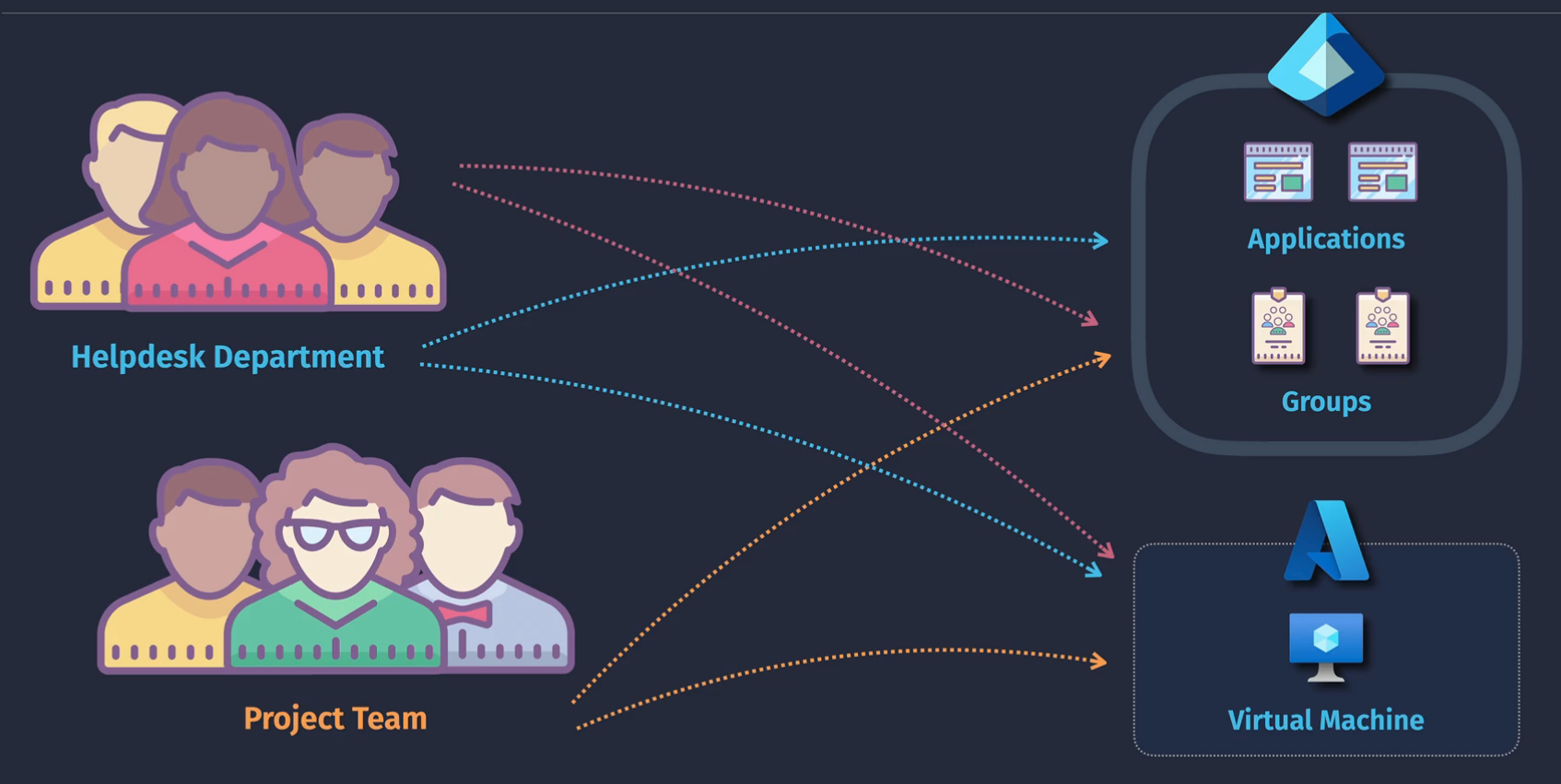
- Teams and groups - user membership reviews
- applications - internal and guest user reviews
- Azure RBAC - PIM - active and eligible
- Entra ID - PIM - active and eligible
Access reviews are the ability to regularly conduct reviews and allow the users and their leaders to verify whether the access is still needed.
Demo - Create and run an access review
- Add user to a role
- Create an access review on the role that you added the user to.
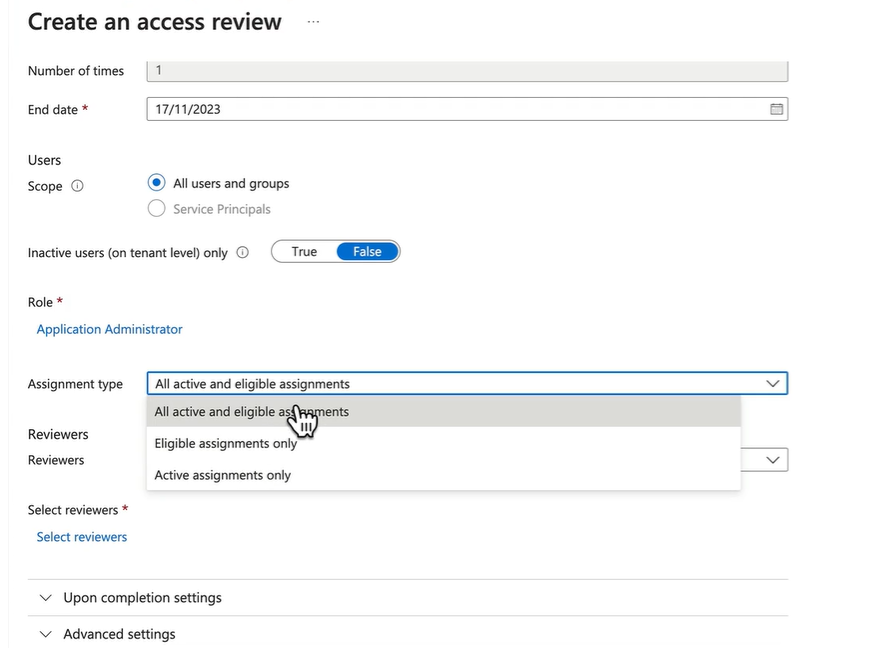
- Self service?
- Members(self) might be a good option
- Manager might be another good option.
- Manually selecting a reviewer might be another good one.
- Click Start
- log in as the user that you want to perform the access review on.
- Perform the self review as the user
- View the results of the review
Entra ID Protection
Entra ID Protection analyzes signals relating to your identities, and measures whether there is any risk (low, medium, or high). In this lesson you'll learn what sort of risks are being identified, and the policies you can configure in ID Protection.
This is only to protect the identity itself, not the resources
Three different types of policies
- Sign in Risk Policy
- User Risk Policy
- MFA Registration Policy - enforce MFA
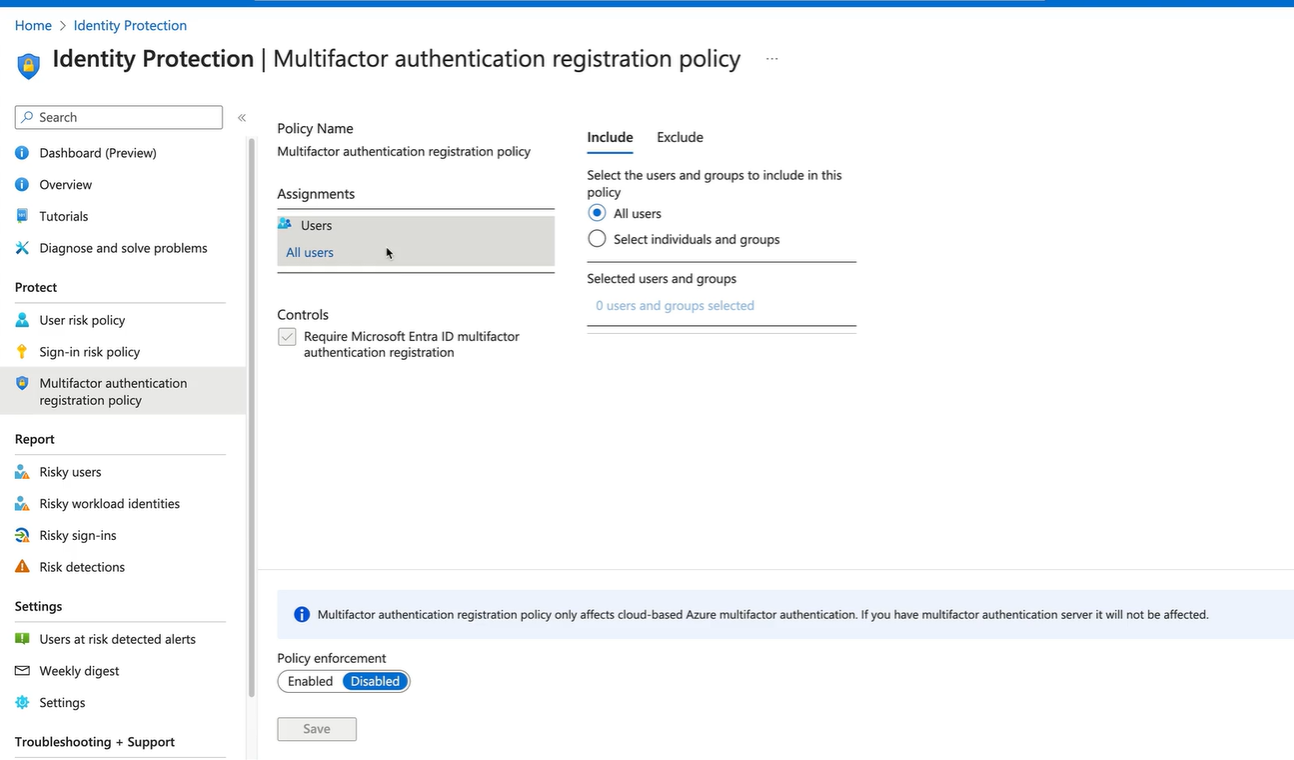
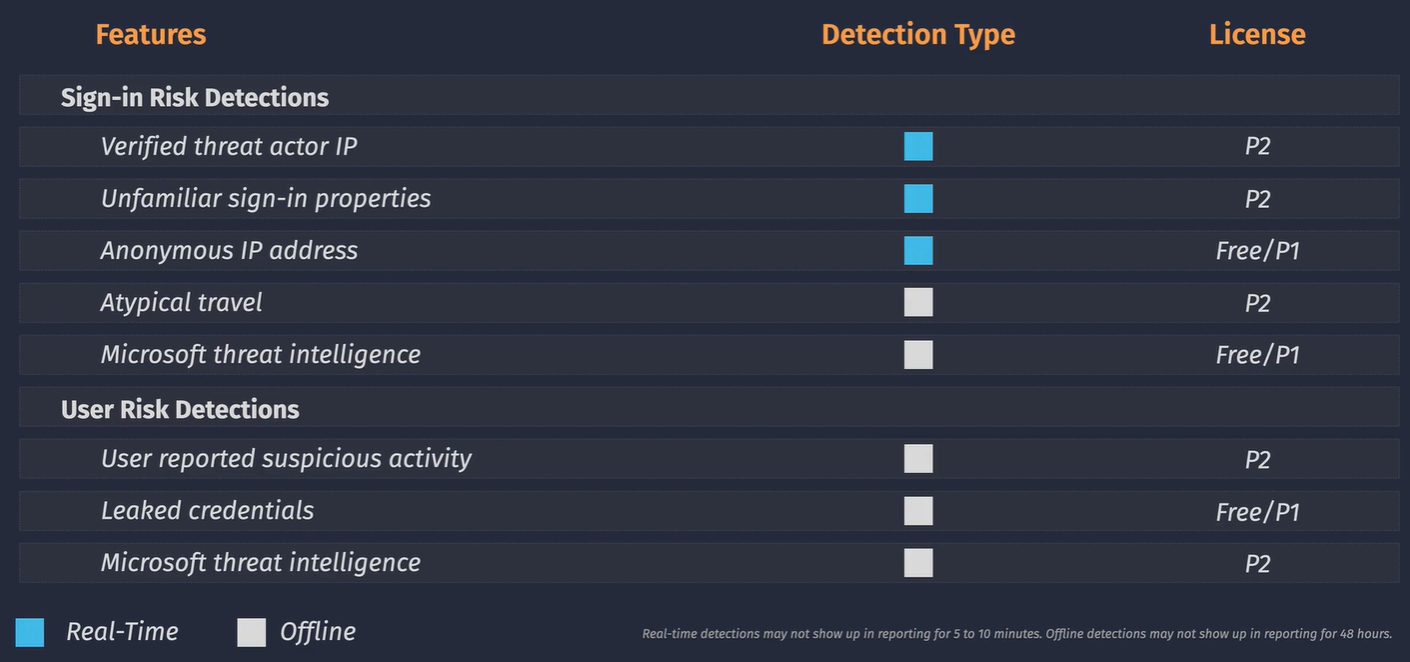
These policies are configured at the tenant level - you can only have one policy of each type configured. You can get greater reporting when using this in conjunction with Conditional Access Policies
Demo - Explore ID Protection Policies
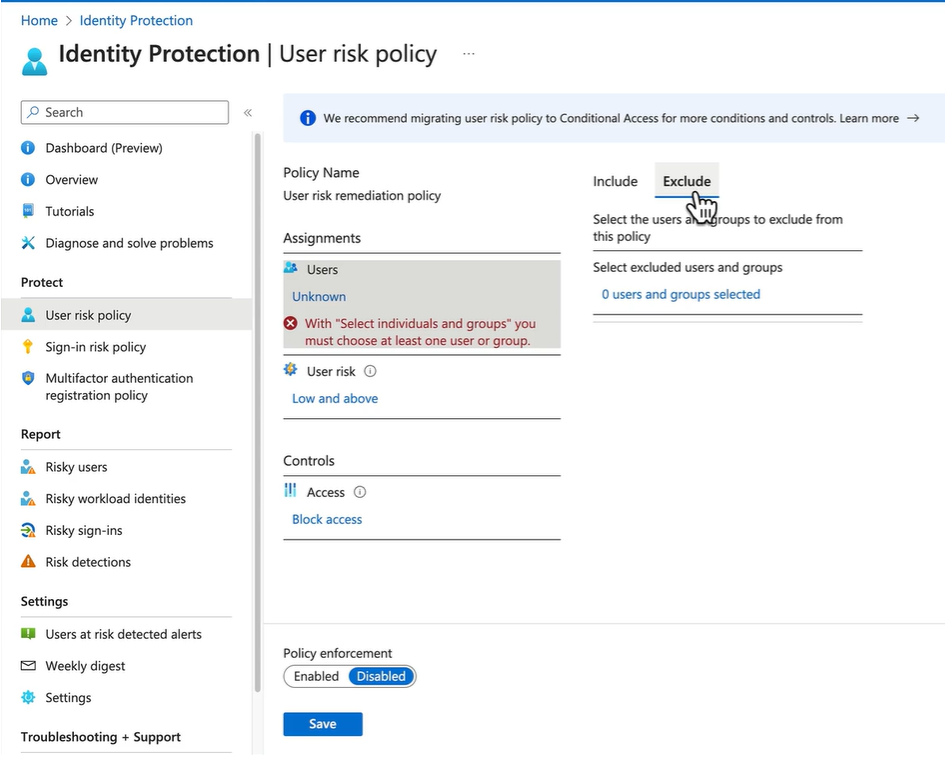 Conditional Access is preferred over User Risk policy
Risks - https://learn.microsoft.com/en-au/entra/id-protection/concept-identity-protection-risks
Conditional Access is preferred over User Risk policy
Risks - https://learn.microsoft.com/en-au/entra/id-protection/concept-identity-protection-risks
Weekly digest might be of some importance:
Entra ID Conditional Access
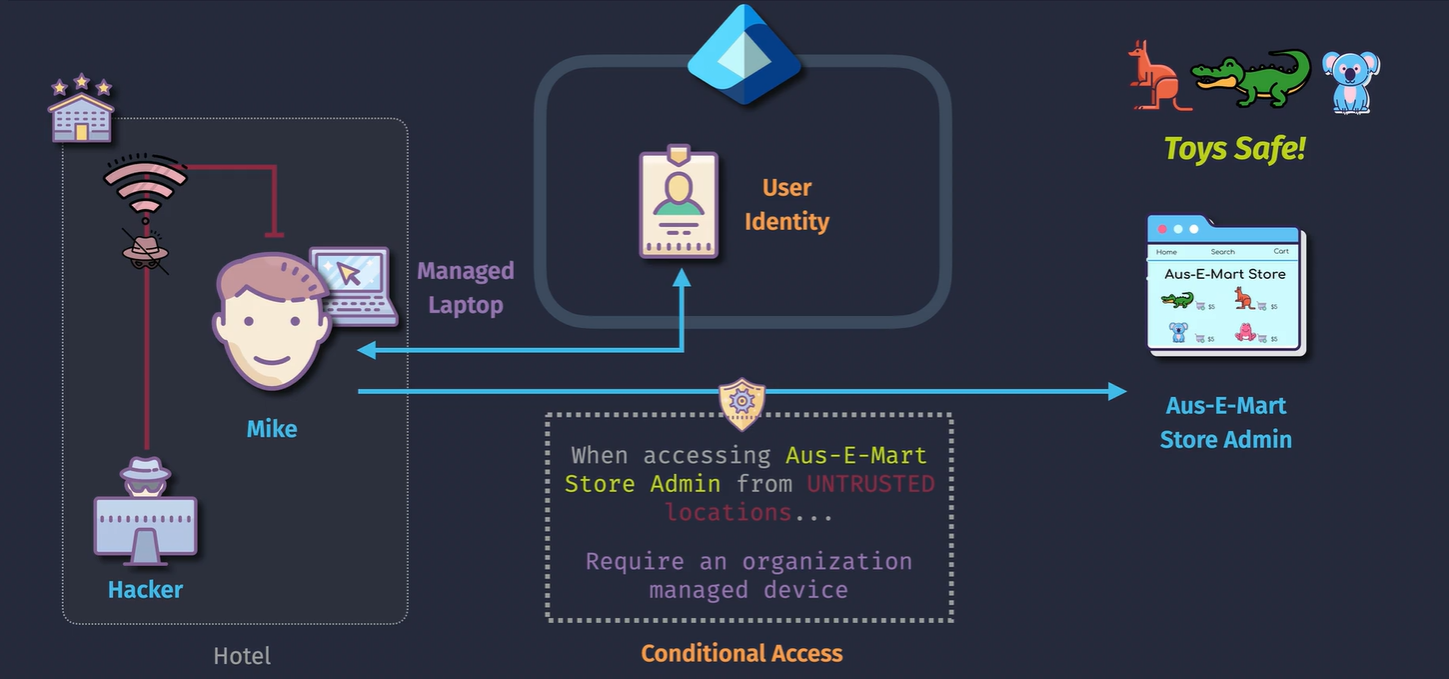
Identities get access to resources WHEN conditions are met.
- Risk
- Location
- Device Platform
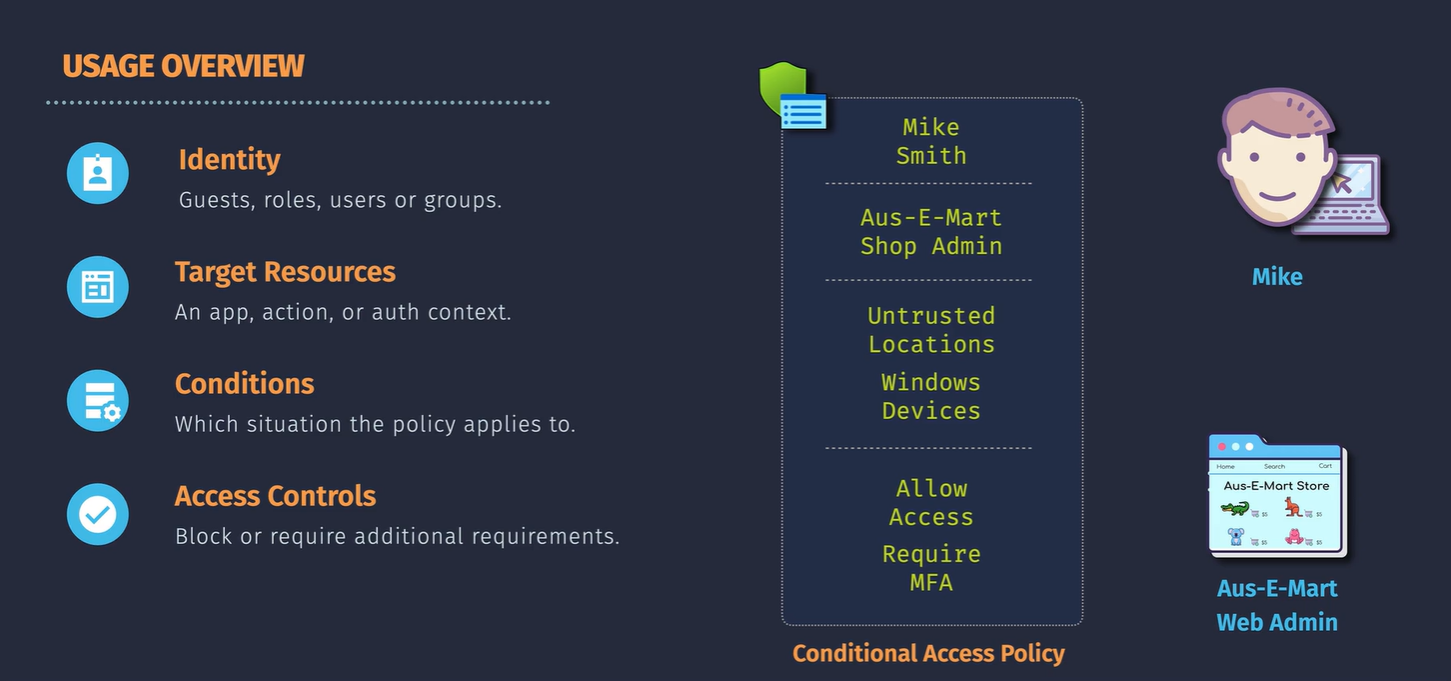
Demo - Configure Conditional Access Policies
Be careful not to create a Conditional Access Policy which locks you out of the Azure Portal :)
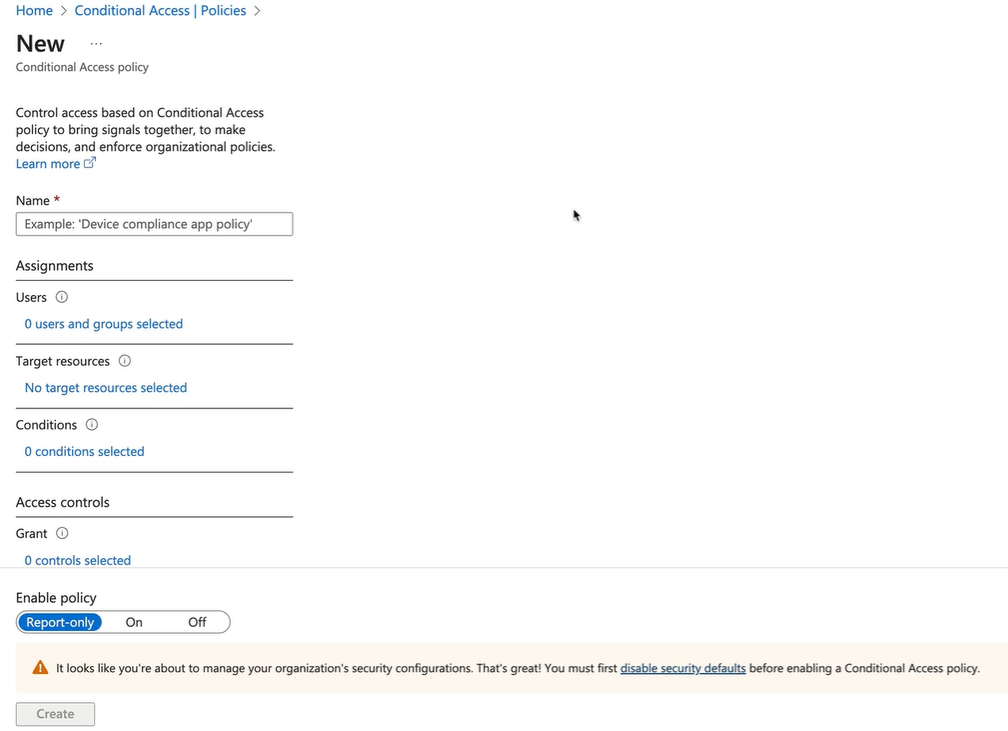
-
Disable the security defaults:
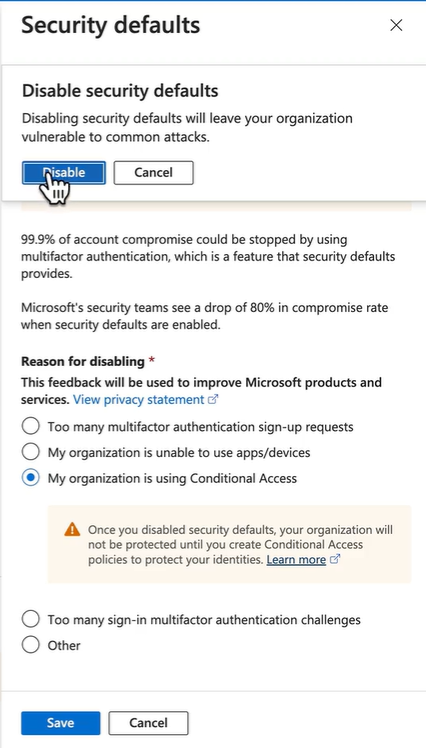
-
Name the policy
-
Select the users to include - all users NOTE: EXCLUDE YOUR MANAGEMENT ACCOUNTS - such as global administrator roles - SO YOU DON'T GET LOCKED OUT
-
Select the application you want to restrict access to - this is to demonstrate without selecting all of Azure.
-
Select conditions:
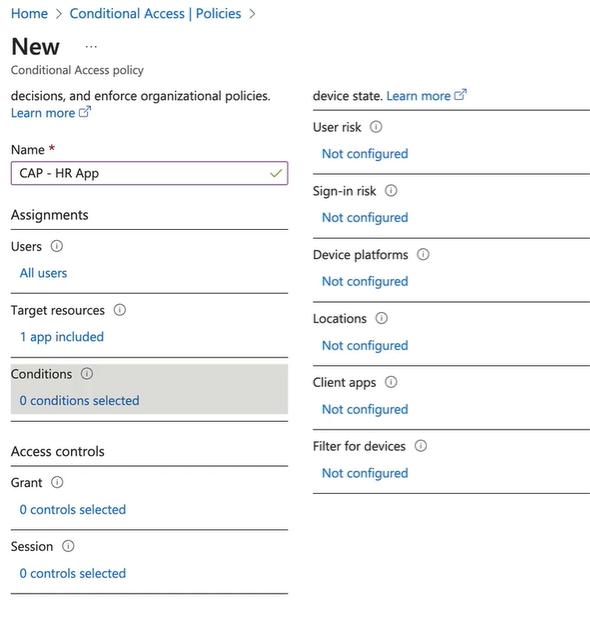
-
Select your grant options:
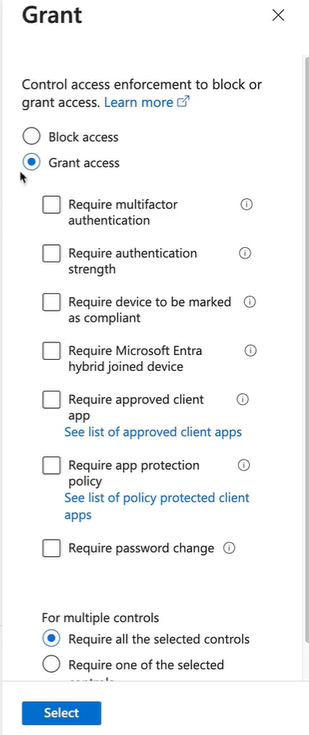
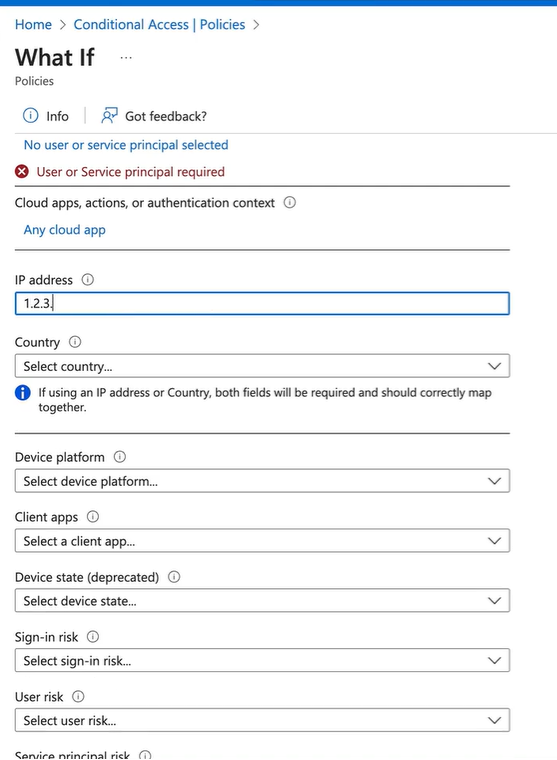
Whatif section
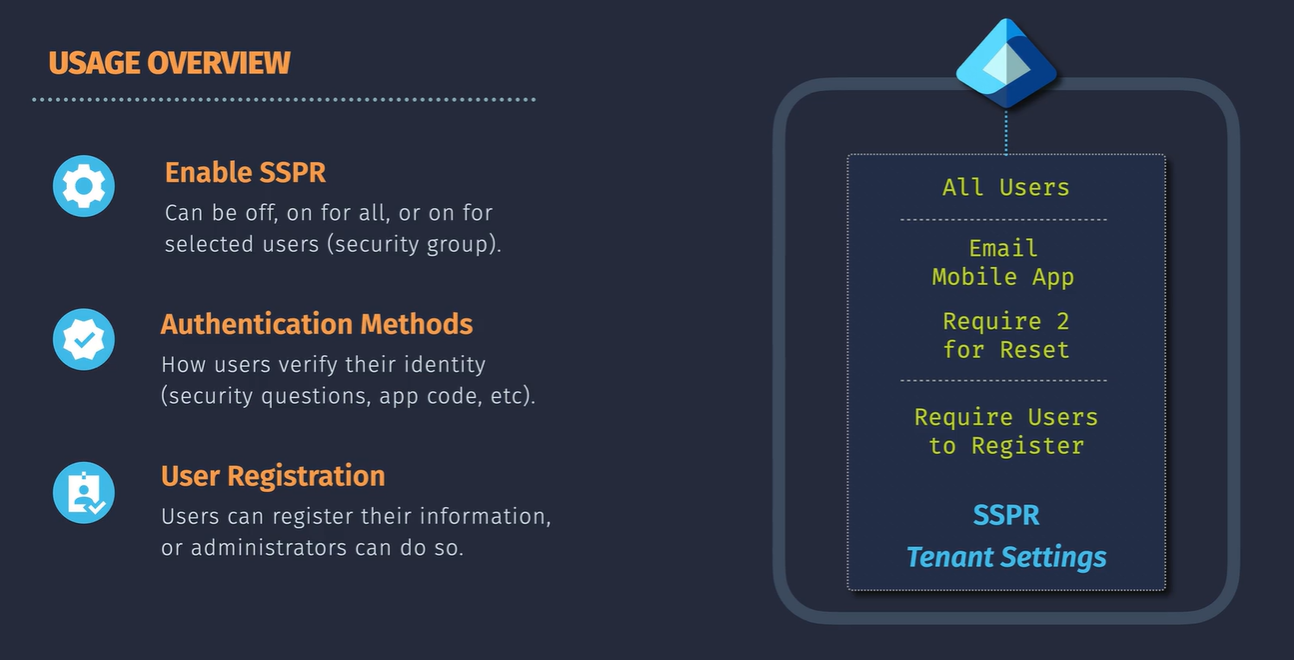
Entra ID Self-Service Password Reset (SSPR)
Allows the user to self reset their own password.
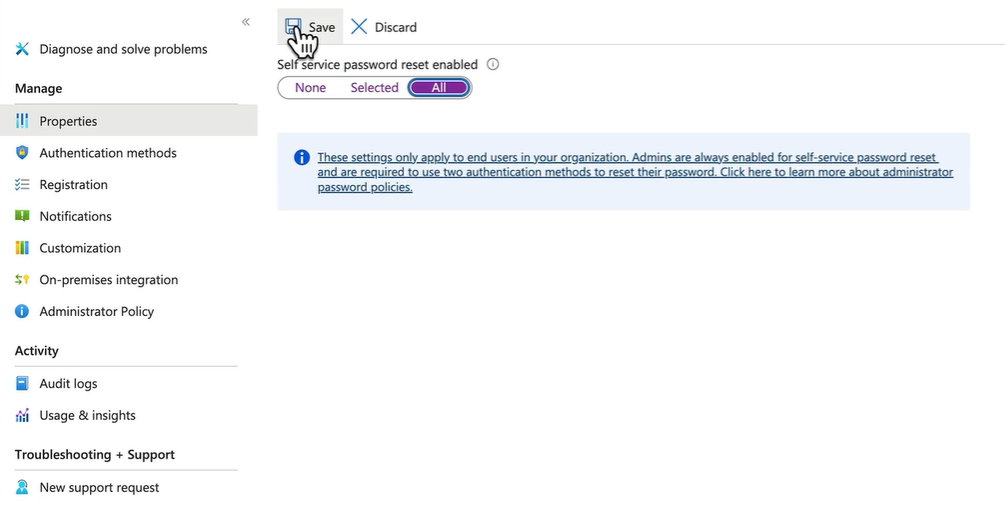
- Enable this for the tenant
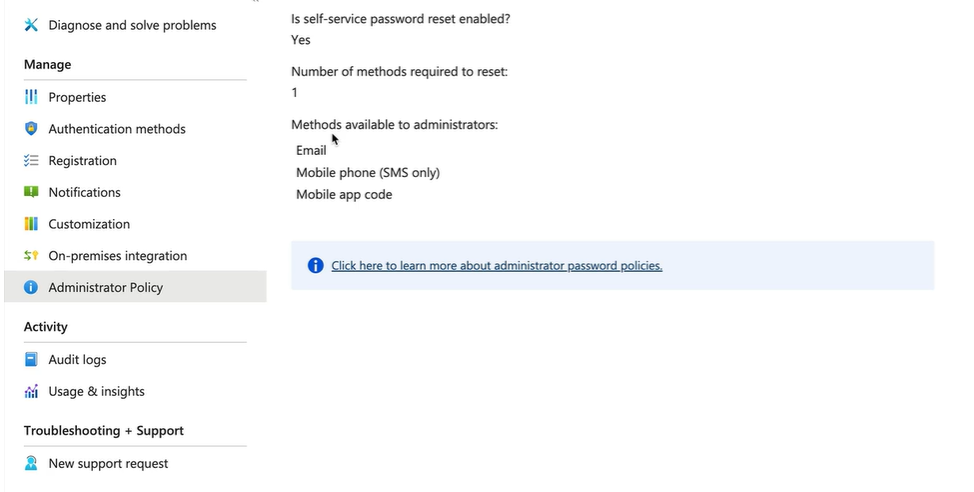
- Auth methods configured for SSPR
- Users Registration
Demo - Configure SSPR
 Security Questions:
Security Questions:
Register:
Password Writeback: Used if you have Entra ID Connect
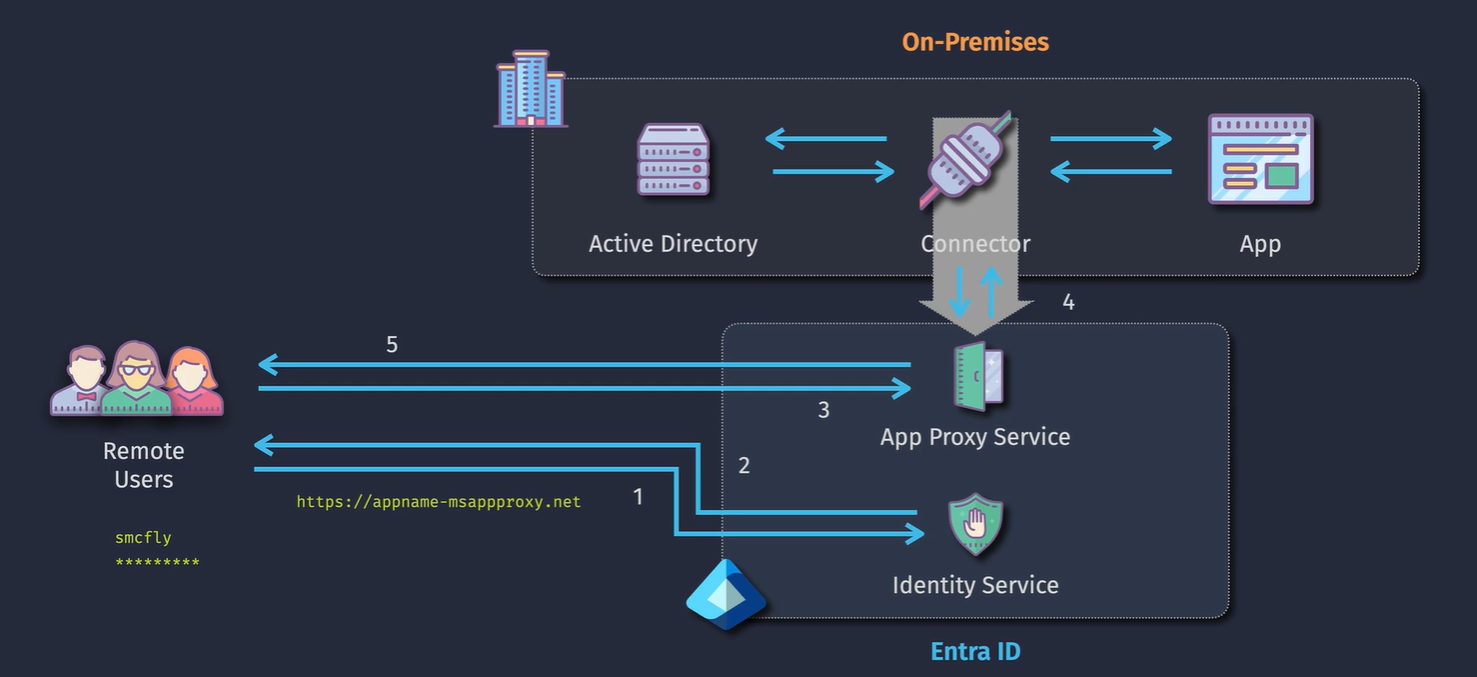
Entra ID App Proxy
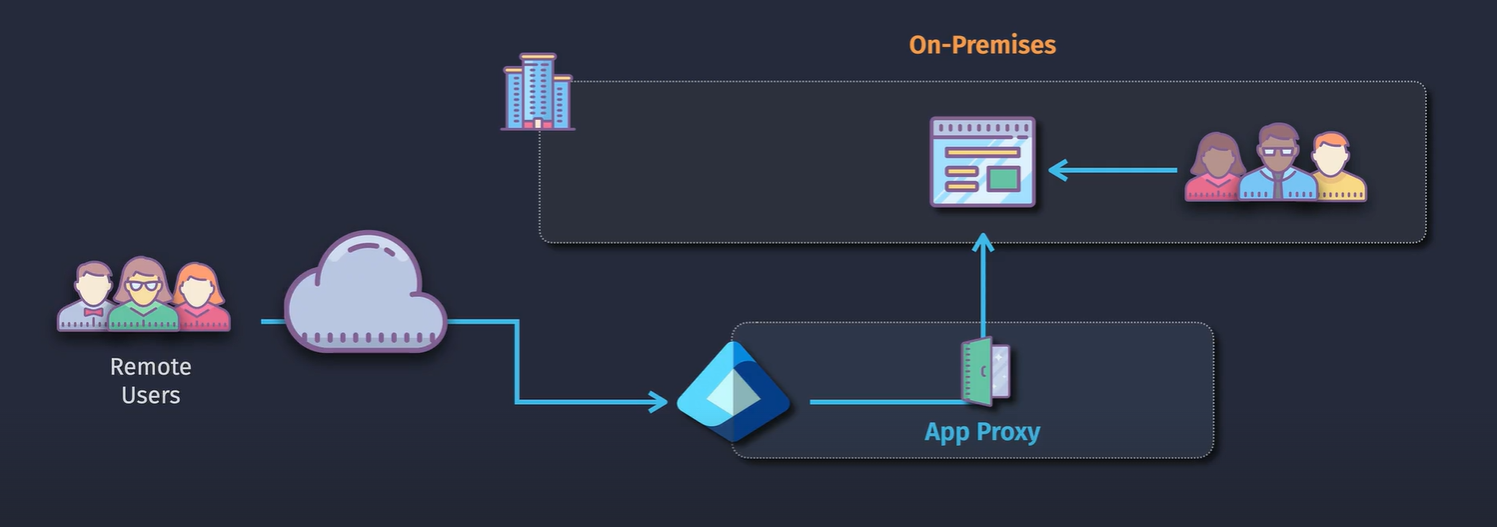
Supported protocols: Integrated windows auth
Components:
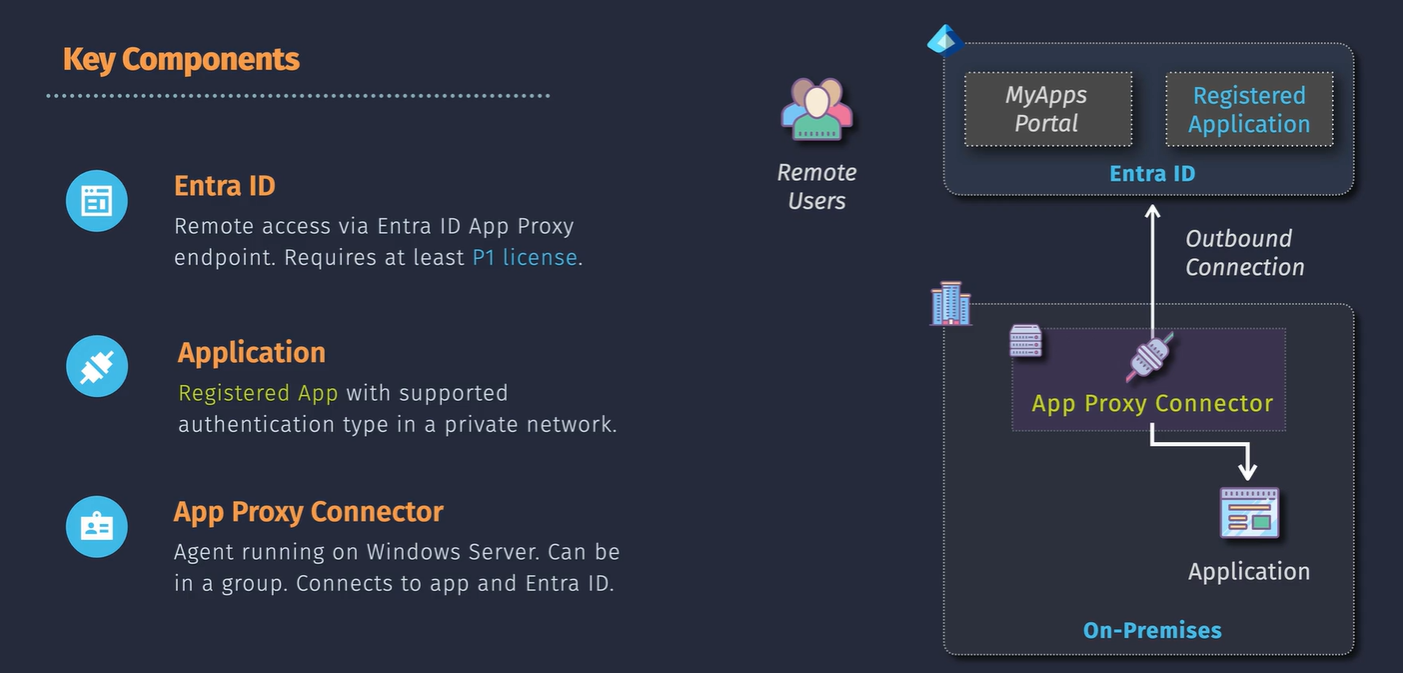 Auth Flow:
Auth Flow:
Demo - Configure Entra ID App Proxy for a Web App
You will need a P1 license here You are going to pretend that the VM is On Prem
- Deploy the template from here: https://portal.azure.com/#create/Microsoft.Template/uri/https%3A%2F%2Fraw.githubusercontent.com%2Fjamesdplee%2Fcloudlee-click2deploy%2Fmain%2Ftemplates%2Fvm-generic.json
- Go to the public IP and the site should load in your browser.
- Delete the access via HTTPS via the NSG that says to allow the inbound HTTP
- RDP into the machine
- Inside the machine, log into Entra ID and click on the Application Proxy option on the left
- Register a new application registration - this will also create an Enterprise Application
- Enabled for sign in, assignment required is disabled, allowed for all users in the Ent App properties,
- Go into the Application Proxy section and fill in the details - make sure you select the correct connector environment.
- Navigate to the fqdn for the app proxy and it should take you to the website.
Case Study - Design Extended Identity Services
Entra P1 Licensing required Moving from off premise to the cloud, looking to decom the rest of it.
Question: How would you provide access to the existing application while decomming the infrastructure?
Solution: Create App Proxy to the application Configure conditional access policies upgrade to premium P2 licensing to support this